The Heartbleed OpenSSL vulnerability has had widespread ramifications, not the least of which is its hit against the virtualization infrastructure many companies implement with VMware. This article explains how to confirm that your VMware hosts and vCenter server are not affected (or affected, as the case may be).
Let’s start with the ESXi host.
- Enable SSH to access the host:
- Login to your vSphere client
- Goto Home | Inventory | Hosts and Clusters
- Highlight your host
- Move to the Configuration tab
- Select Software | Security Profile
- Click Services | Properties
- Scroll down to SSH and then click the Options button
- Click the Start button to initiate the service
- Click OK twice to close the dialog boxes
- Make certain the VMware firewall does not block SSH:
- Continuing in the iSphere client, under Firewall | Properties
- Check the “SSH client” and “SSH server” checkboxes
- Click the OK button to save and close
- Find the host’s management IP address:
- Continuing in the iSphere client, goto Configuration | Networking
- Generally on vSwitch0, look for the IP associated with the “Management Network”
(Note: its possible that you have renamed the default “Management Network” name) - Write down the IP address
- Open a SSH session:
- Using either Putty (in Windows) or SSH (in Linux/OSX), open a connection to your host’s management network
(Note: If you cannot open SSH to the IP, try using the hostname which will work if DNS has been setup.)
- Using either Putty (in Windows) or SSH (in Linux/OSX), open a connection to your host’s management network
- Check the OpenSSL version:
- Once logged in as root via SSH, then…
- Run the following: openssl version -a
- Run to close the SSH session: exit
- Disable SSH access to the host:
- Back in the iSphere client, goto the Configuration tab
- Select Software | Security Profile
- Click Services | Properties
- Scroll down to SSH and then click the Options button
- Click the Stop button to initiate the service
- Click OK twice to close the dialog boxes
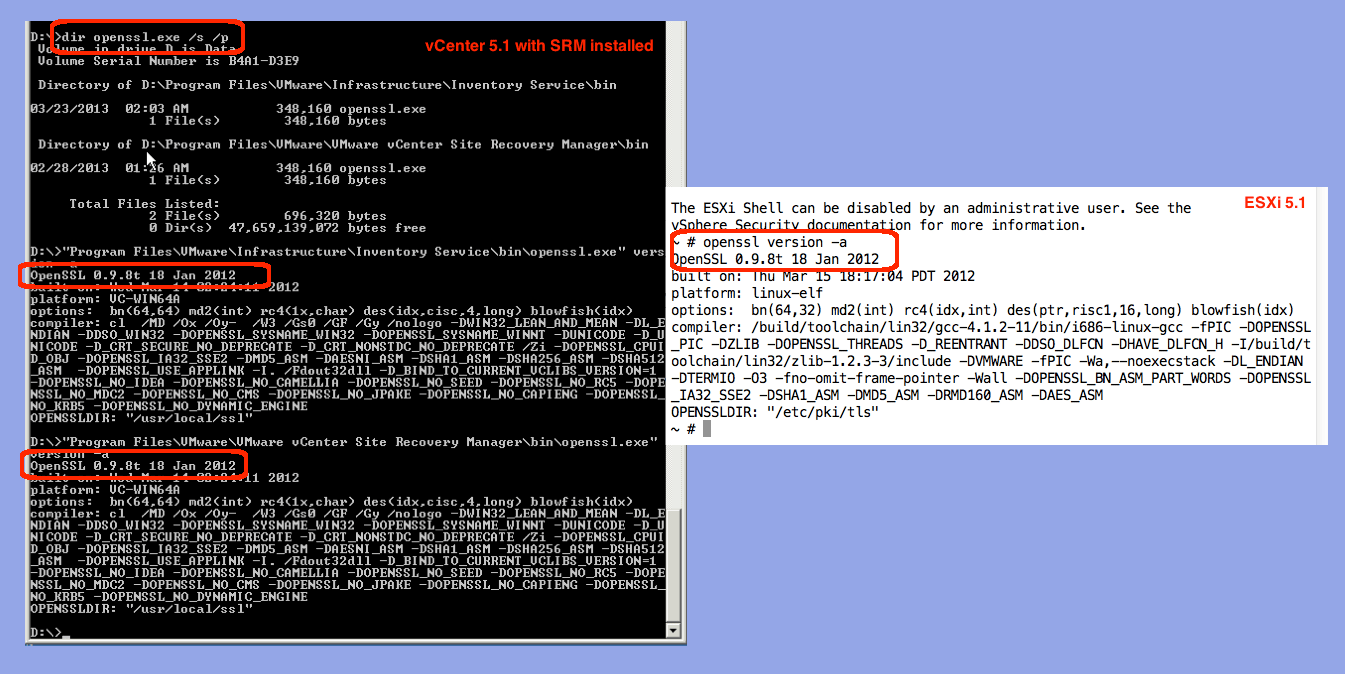
Note that OpenSSL version 0.9.8t is included in VMware 5.1 ESXi, see the screen shot, which means you are not affected. But, VMware 5.5 ESXi does use a vulnerable version. Next, let’s test our vCenter servers. Since you can install various VMware components on the same server, you will want to search for all the instances of “openssl.exe” as your first step.
- Search for all instances of openssl.exe:
- Open a DOS command prompt using Run | cmd.exe
- Move to the root directory: cd \
- Search for OpenSSL: dir openssl.exe /s /p
- Alternative search method (uses Windows Explorer):
- Highlight your c:\ drive
- Type “openssl.exe” (without the quotes) in the search field
- Allow the machine to search… do this for each drive connected to your vCenter server
- For each instance of OpenSSL found:
- Open a DOS command prompt using Run | cmd.exe
- Run the following command for each instance found: filename version -a
Notice that I happen to have my VMware installed on drive d:\ and that since both vCenter and SRM are installed on the same server, there are two files for me to check. As you can see from the screen shots, both are running the older suite and thus are not vulnerable. However, VMware reports that vCenter 5.5 is vulnerable.
See the following link for an updated knowledge base article from VMware regarding all their products they have tested so far: http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2076225